Services
Doorstep service refers to a type of service where a service provider offers their services directly to the customer at their doorstep. The service provider visits the customer's location to provide the requested service, rather than requiring the customer to visit the provider's physical location.
Doorstep services are becoming increasingly popular in many industries, including home repair, Maintenance, AMC,CCTV. With doorstep service, customers can enjoy the convenience of receiving the service they need without having to leave their home or workplace. This can save time and effort and provide a more personalized and convenient experience for customers.

Installation refers to the process of setting up or assembling a new product or system. For example, installation services may include setting up a new computer or installing a new air conditioning unit in a home.
Repair refers to the process of fixing or restoring a product or system that is not working properly. Repair services may include fixing a leaky faucet, replacing a broken window, or repairing a malfunctioning appliance.
Maintenance refers to the process of keeping a product or system in good working order over time. Maintenance services may include regular cleaning, oiling, or other forms of upkeep that help prevent problems before they occur.
AMC stands for Annual Maintenance Contract, which is a contract between a customer and a service provider to provide ongoing maintenance and support for a product or system over a period of time, typically one year. An AMC may include regular maintenance visits, repair services, and other forms of support to ensure that the product or system remains in good working order.

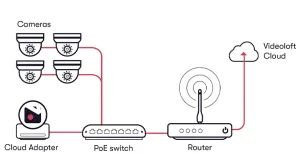
IP-based cameras, also known as network cameras, are a type of video camera that use the Internet Protocol (IP) to transmit video and audio signals over a computer network or the internet. Unlike analog cameras, IP cameras convert the captured video signal into digital data, which can then be transmitted over the network.
IP cameras typically come with built-in web servers, which allows users to access the camera's video feed from a web browser or a mobile app. This makes it possible to monitor a location remotely, from anywhere in the world with an internet connection.
IP cameras offer several advantages over traditional analog cameras, including higher image quality, greater flexibility in terms of placement and installation, and the ability to integrate with other network-based devices and software. Additionally, IP cameras can be configured to send alerts or notifications when motion is detected, making them useful for security and surveillance applications.
Some features of IP-based cameras include:
- High-definition (HD) video resolution
- Night vision and low-light capabilities
- Two-way audio communication
- Motion detection and alerts
- Remote access and monitoring
- Integration with other devices and software, such as video management software or home automation systems.
Overall, IP-based cameras are a powerful and flexible tool for monitoring and securing a variety of locations, from homes and offices to public spaces and industrial facilities.
Audio/video door phones and electronic locks are two types of security devices commonly used in homes, apartments, and other buildings to control access and enhance security.
Audio/Video Door Phones:
Audio/video door phones are intercom systems that allow residents or employees to communicate with visitors before granting access to a building. They consist of a door unit, which typically includes a camera, microphone, and speaker, and an indoor unit, which may include a monitor and intercom for communicating with visitors. Some door phone systems may also include remote unlocking capabilities, allowing users to grant access to visitors from a distance.
Electronic Locks:
Electronic locks are locking mechanisms that are controlled by an electronic signal, rather than a traditional physical key. They may use various forms of authentication, including keypads, biometric sensors, or wireless fobs. Electronic locks can be programmed to provide access to authorized individuals at specific times, and some models may also provide real-time access logs for monitoring and tracking access to a building or room.
Some benefits of audio/video door phones and electronic locks include:
- Enhanced security and control over building access
- Remote access and control capabilities
- Programmable access schedules for specific individuals or groups
- Real-time monitoring and access logs
- Convenience and ease of use for residents or employees.
Overall, audio/video door phones and electronic locks are important security tools that can help protect homes, apartments, and other buildings from unauthorized access and intruders.

EPABX (Electronic Private Automatic Branch Exchange) and IPPABX (Internet Protocol Private Automatic Branch Exchange) are types of intercom systems that are commonly used in office buildings and other large facilities to manage internal communications.
EPABX is a legacy technology that uses analog signals to connect internal phone lines within a private branch exchange (PBX) system. It provides features such as call transfer, call forwarding, and conference calling, which allows employees to communicate with each other and with outside callers using a single, centralized phone system.
IPPABX, on the other hand, uses digital signals and internet protocol (IP) technology to connect internal phone lines. It provides similar features to EPABX, but with greater scalability and flexibility, allowing it to integrate with other IP-based communication systems, such as video conferencing and messaging applications.
Intercom systems, which may be a part of an EPABX or IPPABX system or exist as a standalone solution, are used to communicate internally within a building or facility. Intercom systems typically consist of a master station, which is connected to all of the intercom stations located throughout the building. This allows individuals to communicate with each other through the intercom system, which can be used for tasks such as paging, announcements, and emergency notifications.
Some benefits of EPABX, IPPABX, and intercom systems include:
- Centralized phone and intercom systems for improved communication and collaboration
- Scalability and flexibility to meet the needs of growing businesses and facilities
- Integration with other communication technologies, such as video conferencing and messaging applications
- Enhanced security and safety through emergency notifications and paging capabilities
- Cost-effective solutions for managing internal communications.
Overall, EPABX, IPPABX, and intercom systems are important communication tools for businesses and facilities, providing centralized and scalable solutions for internal communication and collaboration.


A video conferencing system is a technology that enables real-time, face-to-face communication between people who are located in different places. It allows individuals or groups to connect and interact with each other through live video and audio feeds, as well as other features such as screen sharing and virtual whiteboards.
Video conferencing systems typically consist of hardware and software components, which may include:
- Cameras and microphones: These capture and transmit video and audio feeds between participants.
- Displays: These show the video feeds from other participants, as well as other content such as shared screens or presentations.
- Software platforms: These provide the infrastructure and user interface for participants to join and manage video conferences.
Some common features of video conferencing systems include:
- High-quality audio and video feeds to enable clear communication.
- Screen sharing capabilities to allow participants to share their computer screens with other attendees.
- Virtual whiteboards and collaboration tools for interactive sessions.
- Recording and playback capabilities for future reference.
- Integration with other communication technologies such as chat and messaging applications.
Video conferencing systems offer several benefits for businesses and organizations, including:
- Increased productivity and efficiency through remote collaboration.
- Cost savings by reducing travel and associated expenses.
- Improved communication and collaboration between geographically dispersed teams.
- Enhanced work-life balance by enabling remote work and reducing commute times.
- Reduced carbon footprint by reducing the need for travel.
Overall, video conferencing systems are a powerful communication tool that can help businesses and organizations connect and collaborate across different locations, improving productivity and efficiency while reducing costs and environmental impact.

A fire alarm system is a set of interconnected devices designed to detect and alert people in the event of a fire. The system typically includes smoke detectors, heat detectors, manual pull stations, alarm notification devices such as horns or strobe lights, and a control panel.
Here are some key components of a fire alarm system:
Smoke detectors: These devices are designed to detect smoke particles in the air and trigger an alarm when smoke is present.
Heat detectors: These devices are designed to detect rapid temperature changes or high temperatures and trigger an alarm.
Manual pull stations: These are wall-mounted devices that people can use to manually trigger an alarm in the event of a fire.
Alarm notification devices: These devices are designed to alert people to the presence of a fire. They can include horns, sirens, or strobe lights.
Control panel: This is the brains of the fire alarm system. It receives signals from the various sensors and devices and triggers the appropriate alarms.
In addition to these key components, fire alarm systems may also include other features such as voice evacuation systems, which provide audible instructions to occupants of a building in the event of a fire, or emergency lighting systems, which ensure that people can safely exit a building in the event of a power failure.
It's important to regularly test and maintain fire alarm systems to ensure they are working properly and provide adequate protection in the event of a fire.
Biometric attendance solutions are systems that use biometric technology to track and record employee attendance. These systems typically use unique physiological characteristics of an individual, such as their fingerprints, facial recognition, or iris scans, to identify and record employee attendance.
Here are some key components of a biometric attendance solution:
Biometric scanners: These are the devices that capture an employee's biometric data, such as their fingerprints or facial features.
Software: This is the application that processes and analyzes the biometric data to identify an employee and record their attendance.
Database: This is the storage location for the biometric data and attendance records.
Reporting and analytics: This feature allows management to generate reports and analyze attendance data to identify patterns and trends.
Some advantages of using a biometric attendance system include increased accuracy and efficiency, as well as improved security and accountability. Biometric systems can also help prevent time theft and reduce administrative costs associated with manual attendance tracking.
However, it's important to consider potential privacy concerns when implementing a biometric attendance solution. Employers should be transparent about the data being collected and how it will be used and stored, and ensure that they comply with applicable laws and regulations related to biometric data privacy.

An access control system is a security system that restricts access to a physical or virtual space, network, or information. The system typically uses a combination of hardware and software components to manage and control access to a particular area or resource.
Here are some key components of an access control system:
Authentication devices: These devices are used to verify the identity of an individual, such as a key card, pin code, or biometric scanner.
Access control software: This is the software that manages the authentication process and controls access to the system or resource.
Control panel: This is the central hub of the access control system, which receives input from authentication devices and decides whether to grant or deny access.
Door locks and readers: These are the physical components that are installed at entry points to restrict access.
Monitoring and reporting tools: These features allow management to monitor and track access to the system or resource, and generate reports on access history and activity.
Some advantages of using an access control system include increased security, improved efficiency and convenience, and the ability to restrict access to sensitive areas or resources. Access control systems can also help prevent unauthorized access and reduce the risk of theft, vandalism, or other security breaches.
However, it's important to consider potential vulnerabilities in the system, such as hacking or physical tampering. It's also important to properly train employees on how to use the system and ensure that it complies with applicable laws and regulations related to data privacy and security

Mobile network boosters and jammers are two very different types of devices that serve different purposes.
A mobile network booster, also known as a signal booster or repeater, is a device that amplifies and enhances the signal strength of a mobile network. It is designed to improve the quality of cellular signals and extend coverage to areas where the signal may be weak or non-existent. The device typically consists of an external antenna, an amplifier, and an internal antenna.
On the other hand, a mobile network jammer, also known as a cell phone jammer or signal blocker, is a device that disrupts cellular communication by emitting radio frequency signals that interfere with the signal between the mobile device and the network. The purpose of a jammer is to prevent mobile devices from sending or receiving signals within a certain radius, which could be used for security reasons or to prevent nuisance or disruptive behavior in certain settings.
It's important to note that the use of jammers is illegal in many countries, including the United States. Jamming mobile signals is a violation of the Federal Communications Commission (FCC) regulations and could result in significant fines or even imprisonment. The use of mobile signal boosters, on the other hand, is legal in most countries, as long as they comply with local regulations and are not causing interference with other devices or networks.

A burglar or intrusion alarm system is a security system designed to detect unauthorized entry into a building or property. The system typically includes sensors, control panels, and alarm notification devices, and may be connected to a monitoring service or directly to emergency services.
Here are some key components of a burglar or intrusion alarm system:
Sensors: These devices are used to detect movement, door or window opening, glass breakage, or other signs of intrusion. Sensors can be wired or wireless and can be installed both indoors and outdoors.
Control panel: This is the central hub of the system, which receives input from sensors and decides whether to trigger an alarm. The control panel may also be used to arm or disarm the system.
Alarm notification devices: These devices are designed to alert people to the presence of an intruder, and can include sirens, strobe lights, or other audible or visual alarms.
Monitoring service: This is an optional feature that connects the alarm system to a monitoring center, which can dispatch emergency services or contact designated personnel in the event of an alarm.
Some advantages of using a burglar or intrusion alarm system include increased security, improved peace of mind, and the ability to deter intruders. Alarm systems can also provide evidence in the event of a break-in, which can be useful for insurance purposes or for criminal investigations.
However, it's important to properly install and maintain the system, and to ensure that it complies with applicable laws and regulations related to data privacy and security. False alarms can also be a concern, as they can lead to fines or other penalties and can waste emergency services' resources.

Home or office automation, also known as smart home or smart office technology, refers to the integration of various devices and systems to provide automated control and monitoring of a home or office environment. The goal of automation is to improve efficiency, convenience, and security, and to reduce energy consumption and costs.
Here are some examples of devices and systems that can be integrated into a home or office automation system:
Lighting: Smart lighting systems can be programmed to turn lights on and off, adjust brightness, or change colors based on a schedule or specific triggers, such as motion detection or voice commands.
Climate control: Smart thermostats can be used to adjust temperature and humidity levels based on occupancy, time of day, or weather conditions. Some systems can also detect and adjust for individual preferences.
Entertainment: Smart entertainment systems can be used to control audio and video devices, such as televisions, speakers, and streaming services, from a single interface.
Security: Smart security systems can include cameras, door locks, motion detectors, and alarms, which can be monitored and controlled remotely via a mobile app.
Energy management: Smart energy systems can monitor and control energy consumption, and can help reduce energy waste and costs.
Some advantages of using a home or office automation system include increased comfort, convenience, and security, and the ability to save time and money by optimizing energy usage. Automation systems can also be programmed to perform routine tasks automatically, reducing the need for manual input and freeing up time for other tasks.
However, it's important to ensure that the system is properly installed and configured, and that it complies with applicable laws and regulations related to data privacy and security. It's also important to consider potential vulnerabilities in the system, such as hacking or physical tampering. Proper user training is also important to ensure that the system is used safely and effectively.

A motion detection sensor is a type of electronic device that is designed to detect movement in a given area. These sensors are commonly used in security systems, lighting systems, and other automated systems that require the detection of motion.
There are several types of motion detection sensors, including:
Passive Infrared (PIR) sensors: These sensors detect changes in temperature, such as the movement of a warm body, and trigger an alarm or activate a device.
Ultrasonic sensors: These sensors emit high-frequency sound waves that bounce off of objects in a room, and detect movement based on changes in the pattern of reflected waves.
Microwave sensors: These sensors emit low-power microwave signals that detect motion based on changes in the frequency or wavelength of the reflected signal.
Video motion sensors: These sensors use cameras and video analytics software to detect motion based on changes in the video image, such as movement of objects or changes in light levels.
Motion detection sensors can be used in a variety of applications, such as activating lighting systems in response to movement, triggering an alarm in a security system, or turning on a video camera when motion is detected. Some sensors can also be programmed to detect specific types of motion, such as human movement, to reduce false alarms and improve accuracy.
It's important to properly install and maintain motion detection sensors, and to ensure that they comply with applicable laws and regulations related to data privacy and security. False alarms can also be a concern, as they can lead to fines or other penalties and can waste emergency services' resources.

An automatic boom barrier is a type of gate that is used to control vehicular access to a restricted area, such as a parking lot, gated community, or commercial facility. The barrier consists of a metal arm or boom that pivots on a horizontal axis, and is raised or lowered to allow or restrict access to the area.
Here are some key components of an automatic boom barrier system:
Boom: This is the metal arm that spans the width of the entrance or exit, and is raised or lowered to allow or restrict access. The boom is typically made of aluminum or steel, and can be up to 8 meters long.
Motor: This is the mechanism that raises and lowers the boom, and is typically powered by an electric motor.
Control panel: This is the central hub of the system, which receives input from sensors and decides whether to raise or lower the boom. The control panel may also be used to program the system, set access restrictions, or view system status.
Sensors: These devices are used to detect vehicles approaching the barrier, and can include loop detectors, infrared sensors, or ultrasonic sensors.
Access control system: This is an optional feature that can be used to restrict access to the area, and can include keypads, card readers, or biometric readers.
Some advantages of using an automatic boom barrier system include improved security, increased control over access to the area, and reduced risk of accidents or unauthorized entry. The system can also be integrated with other security systems, such as surveillance cameras or alarm systems.
However, it's important to properly install and maintain the system, and to ensure that it complies with applicable laws and regulations related to safety and accessibility. It's also important to consider potential vulnerabilities in the system, such as hacking or physical tampering, and to take steps to mitigate these risks.

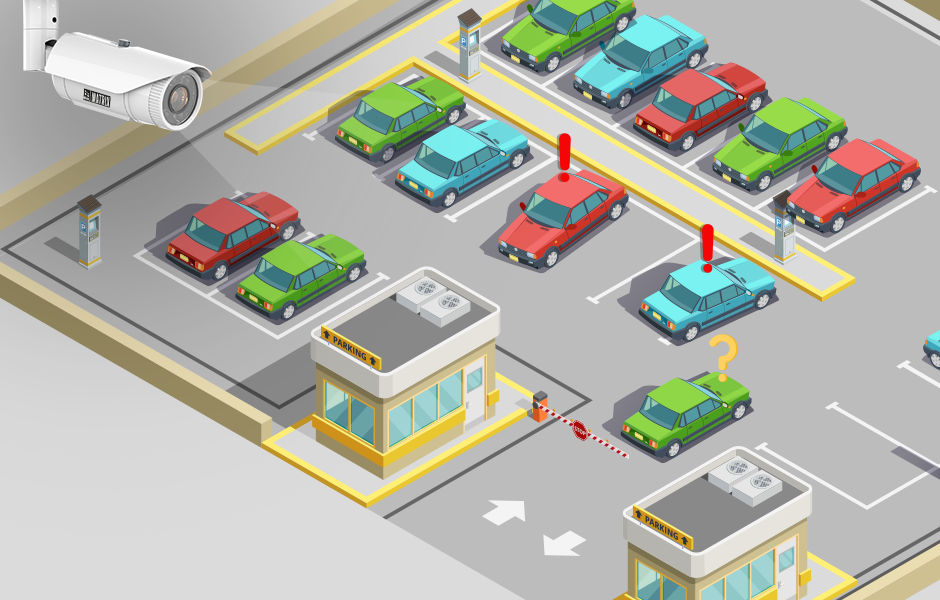
A parking management system is a set of hardware and software tools that are used to manage and control parking facilities. These systems can be used in a variety of settings, such as public parking garages, office buildings, or shopping centers.
Here are some key components of a parking management system:
Parking meters: These are devices that are used to collect payment from drivers for parking. They may be coin-operated, or they may accept credit card payments or mobile payments.
Parking guidance system: This is a system that uses sensors and LED displays to guide drivers to available parking spaces. It can reduce traffic congestion and help drivers save time and fuel.
Automated ticket dispensers: These devices issue tickets to drivers when they enter the parking facility. The tickets may include information such as the time and date of entry, the location of the parking spot, and the fee for parking.
License plate recognition system: This is a system that uses cameras to capture images of license plates as vehicles enter or exit the parking facility. This information can be used to identify vehicles that have overstayed their allotted parking time, or to track parking patterns over time.
Parking management software: This is the software that controls the parking management system, and provides a central point for monitoring and managing the system. It can include features such as real-time occupancy tracking, revenue reporting, and customer service tools.
A parking management system can provide a number of benefits, including increased revenue, improved customer satisfaction, and reduced labor costs. However, it's important to properly install and maintain the system, and to ensure that it complies with applicable laws and regulations related to privacy, accessibility, and safety.
Computers are electronic devices that are designed to receive, store, process, and output data. They are used in a wide variety of settings, including homes, businesses, schools, and government offices.
Here are some key components of a computer:
Central Processing Unit (CPU): This is the "brain" of the computer that performs the instructions and calculations necessary for processing data.
Random Access Memory (RAM): This is the temporary memory that the computer uses to store data and instructions that it needs to access quickly.
Hard Disk Drive (HDD) or Solid State Drive (SSD): This is the long-term storage device where the computer stores files and programs that it will use over an extended period of time.
Input devices: These devices allow the user to interact with the computer and input data, including keyboards, mice, touchpads, and touchscreens.
Output devices: These devices allow the computer to display data and output information, including monitors, printers, and speakers.
Operating System (OS): This is the software that manages the computer's hardware and provides a platform for running applications. Examples of popular operating systems include Windows, macOS, and Linux.
Computers can be used for a wide variety of tasks, including word processing, data entry, graphics design, video editing, and gaming. They can also be used to access the internet and communicate with other people around the world.
While computers can provide many benefits, they also come with some risks, such as cybersecurity threats, privacy concerns, and potential negative impacts on mental and physical health. It's important to use computers responsibly and take steps to protect personal information and devices from harm.

Networking refers to the practice of connecting multiple devices, such as computers, servers, and mobile devices, together to facilitate communication and data exchange. Networks can be used in a variety of settings, including homes, businesses, and academic institutions.
Here are some key components of a network:
Network devices: These devices are used to connect the different components of a network, including routers, switches, and hubs.
Network protocols: These are the rules and procedures that govern the way data is transmitted and received over a network. Some common network protocols include TCP/IP, HTTP, and FTP.
Network topology: This refers to the physical or logical layout of a network, including the way devices are connected and the paths that data takes to travel between them.
Network security: This involves implementing measures to protect the network and its devices from unauthorized access, data breaches, and other security threats.
Network management: This involves monitoring and maintaining the network to ensure that it is running smoothly and efficiently.
Networks can provide a variety of benefits, including improved communication and collaboration, increased efficiency, and enhanced access to information and resources. However, they also come with some risks, such as security threats and the potential for downtime or service interruptions. It's important to take steps to secure and maintain networks to ensure that they continue to provide value and function as intended.

All Copyright © Reserved To Computer Doctor Zone

